Warning
All statements in this document reflect a "default" Brainspace Application server installation and do not necessarily reflect all deployments and environments.
Many of the default design and configuration settings directly affect the security of the Brainspace Application server. Making changes to the default settings or architecture can potentially open vulnerabilities that may be leveraged by unauthorized users to access data in your Brainspace application.
How Brainspace Application Server Uses HAProxy
Brainspace Application Services - Click image to view full-size
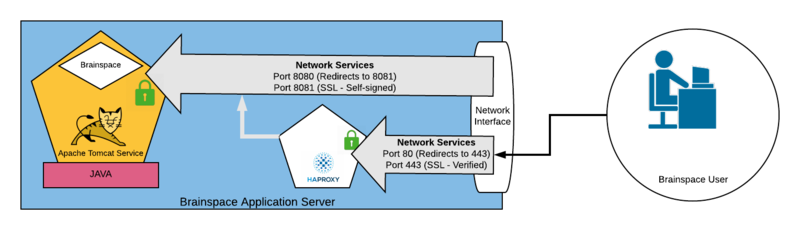
Technical Detail
Brainspace users access the application through a web browser using the https protocol. For example: "https://brainspace.domain.com/". The https protocol, by default will connect to the server over port 443.
When connecting to Brainspace this way, you are actually connecting to the HAProxy service. Internally HAProxy "proxies" your connection to the Tomcat service that listens on port 8081 using a self-signed ssl certificate that is generated during the Brainspace installation process. Some customers may choose to replace the self-signed certificate with their own provided commercial certificate.
Any connections made over the insecure http protocol, will be automatically redirected to the secure https protocol.
Purpose & Function
HAProxy provides several services to enhance functionality and elevate security when accessing the Brainspace Application server.
Service | Description |
|---|---|
Default Web Service Ports | The Brainspace Tomcat application service runs as an unprivileged user and therefore is unable to use the default HTTP (port 80) or HTTPS (port 443) service ports. HAProxy has the ability to run in a secure (chroot or sandbox) mode as an unprivileged user while still using the privileged "default" network ports that are expected by an Internet browser like Google Chrome or Microsoft Edge. |
TLS 1.2 Security and Verified SSL Certificate | Back-end communication between the Brainspace server roles is encrypted using a self-signed SSL certificate. This type of certificate provides encryption, however it does not provide a validated certificate connection. This will cause the user's browser to show a security error message. HAProxy performs TLS encryption to the end user with an *optional validated certificate over the TLS 1.2 standard protocol. * Validated certificates are not provided or installed by default and must be supplied by the domain owner. |
Security Rule Headers | In order to meet the highest security standards, we utilize HAProxy to insert several security headers such as `X-Frame-Options` and CORS Security rules. |
Soft-Fail Message | If the Tomcat service is down or unreachable, HAProxy will display a user-friendly message to the end users. |
Optional Configuration: External Load Balancer Best Practices
In environments that use a network load balancer appliance such as an F5 Big-IP or Netscaler, it may be preferred, or required, to proxy connections to Brainspace through these devices. If using a load balancer or other proxy device to access Brainspace, it is recommended that the load balancer be configured to use HAProxy and handle any required SSL off-loading.
While Brainspace does not support load balancer configurations, here are some best practices to follow when configuring a load balancer or proxy. If your organization's security requirements differ, please consult with Brainspace Support and use your own configuration as necessary.
Configure the load balancer to connect to the Brainspace Application over port 80 (http/non-ssl) and 443 (https/ssl) .
Configure the load balancer to allow an unverified or self-signed SSL certificate when communicating with the Brainspace Application server on port 443.
Set the connection timeout for a minimum of 5 minutes.
Use SSL acceleration on the load balancer with a verified SSL certificate.
Only allow connection to the front-end that are TLS 1.2 or higher.
Use only strong cryptographic cyphers for the TLS encryption.
Important
X-Forwarded-For Requirement
When using a load balancer, you MUST set the X-Forwarded-For header that provides the IP address for the end user. Failure to set this header will result in a clickjacking security check that will cause login to Brainspace to fail.
Additional References: