Graph API Connector Prerequisites
Overview
Reveal supports integration with Microsoft Osuite for in-place preservation and data collection. This document describes the prerequisites for integrating Reveal with Microsoft Osuite.
Information Required for Integration
The following details are required for configuring o365 Office connector in Reveal.
Service account username and password which has been assigned the following roles:
eDiscovery Manager
Note
Disable Multi factor Authentication for the service account and make sure Service account has E5 License assigned to it.
Client ID and Tenant ID of the registered application in Azure.
Client secret generated for the application.
Check whether we have License for Tenant as Microsoft Entra ID P2.
The below sections describe the steps to be carried out in o365 Office for integration with Reveal.
Create a Service Account in Office 365
To create a new Office 365 user, go to Users >Active users in the Office 365 admin center and click on Add a User.
Enter the details of the new user and click Finish Adding. The user will now appear in the list of active users.
Navigate to Microsoft Purview. Go to Settings and click on Role Groups. Click on eDiscovery Manager and click on Edit.
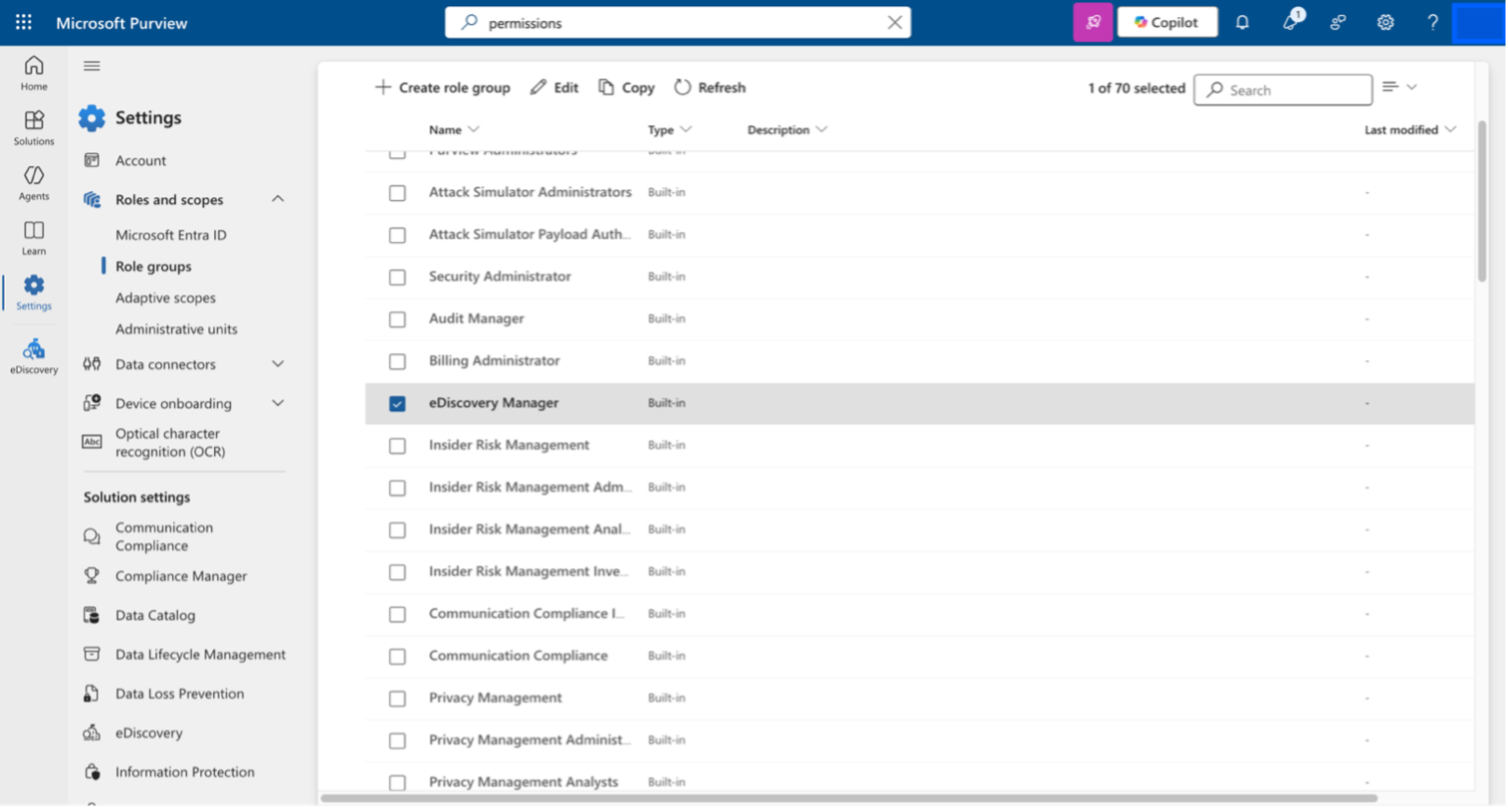
Figure: Edit eDiscovery Manager
Search for the service account to be added under eDiscovery Manager. Choose the service.
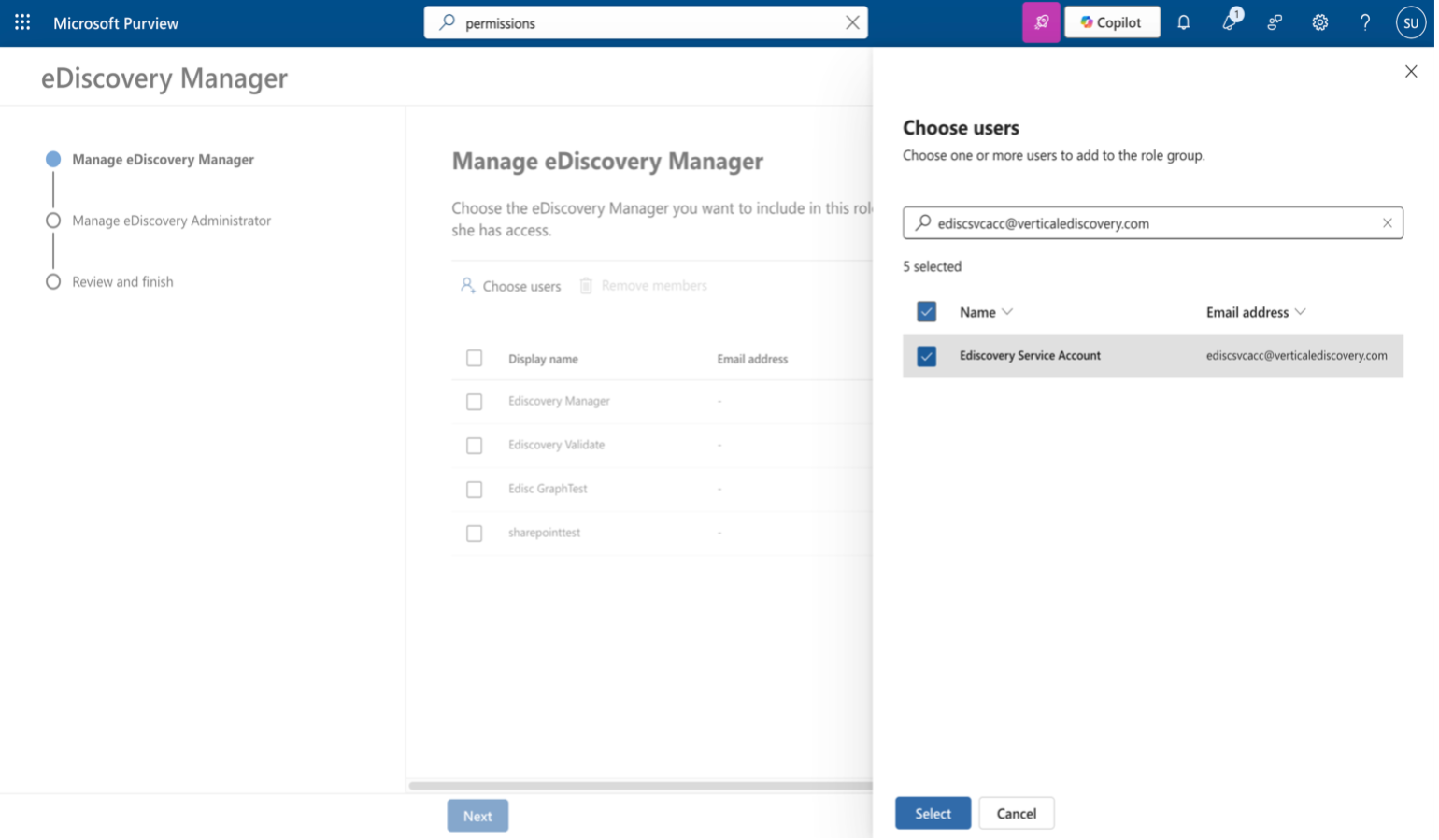
Figure: Add Service Accounts to eDiscovery Manager
Click on Next in Manage eDiscovery Administrator and click on Done.
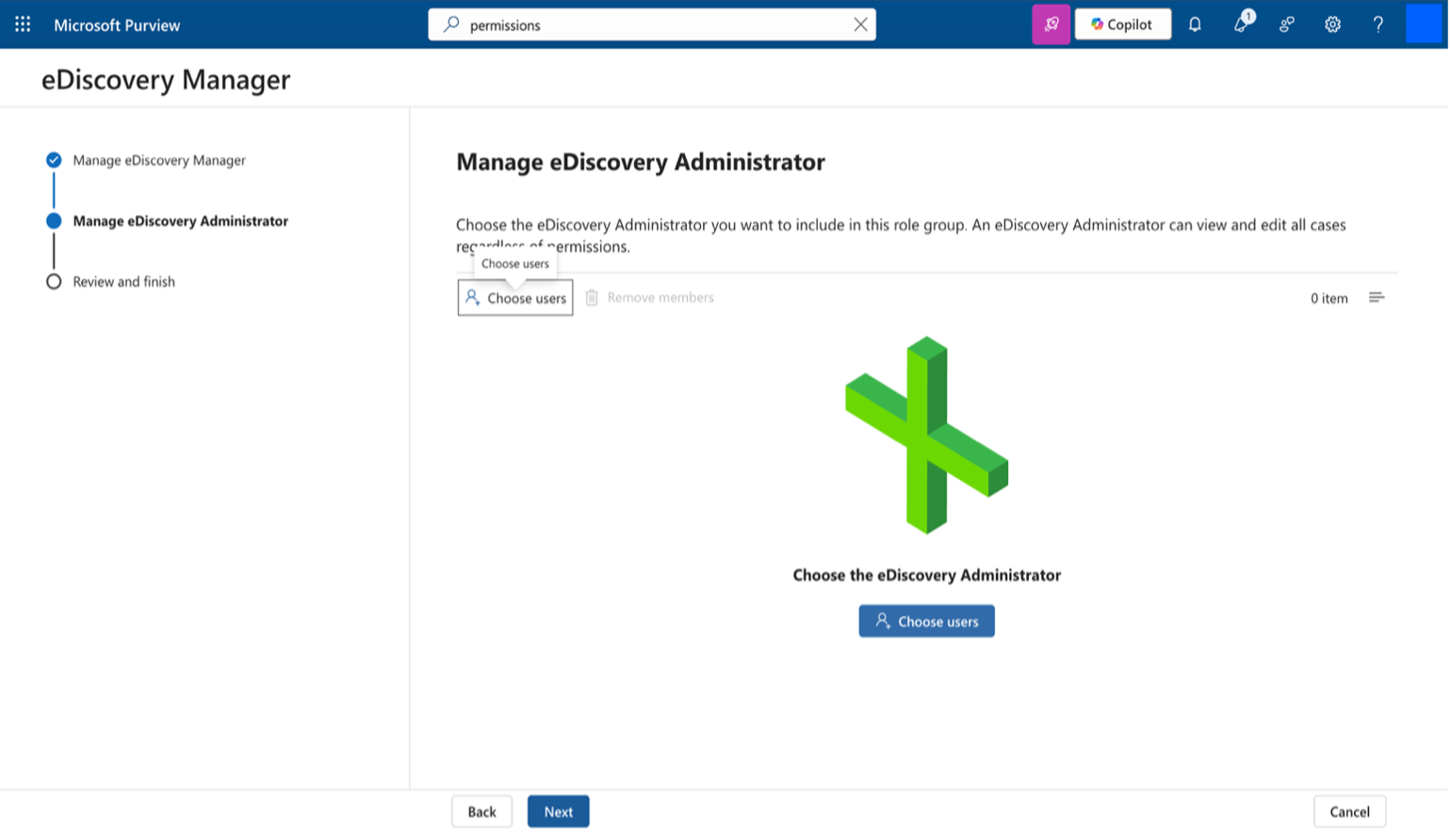
Register Application in Azure
Registering an application establishes a trust relationship between the app and the Microsoft identity platform. The trust is unidirectional: the app trusts the Microsoft identity platform, and not the other way around.
Follow the steps given below to create the app registration:
Sign in to the Azure portal.
If access to multiple tenants is available, from the top menu, use the Directory + subscription filter to select the tenant in which the application is to be registered.
Search for and select Microsoft Entra ID.
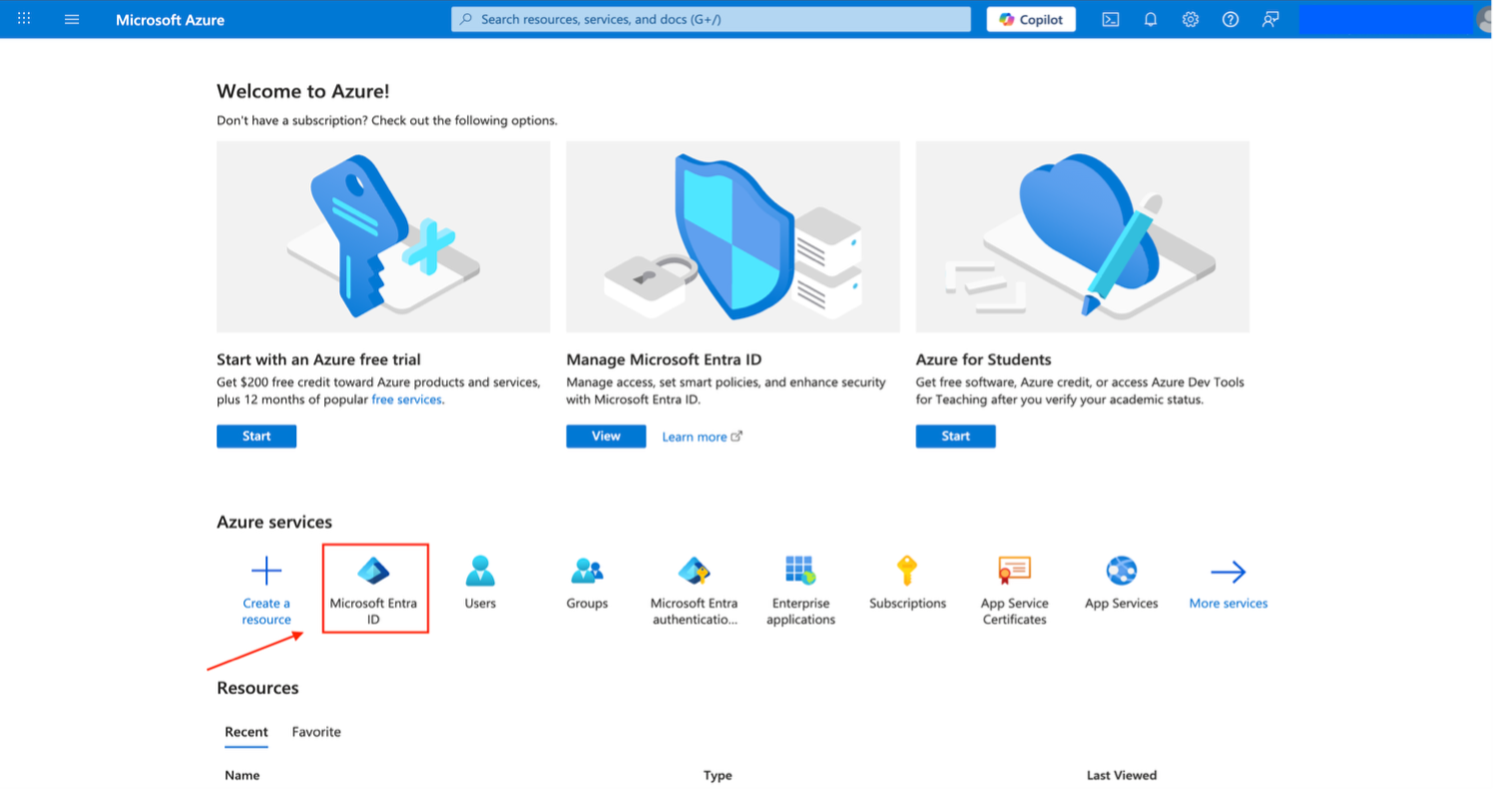
Figure: Microsoft Azure Services
Under Manage, select App registrations > New registration.
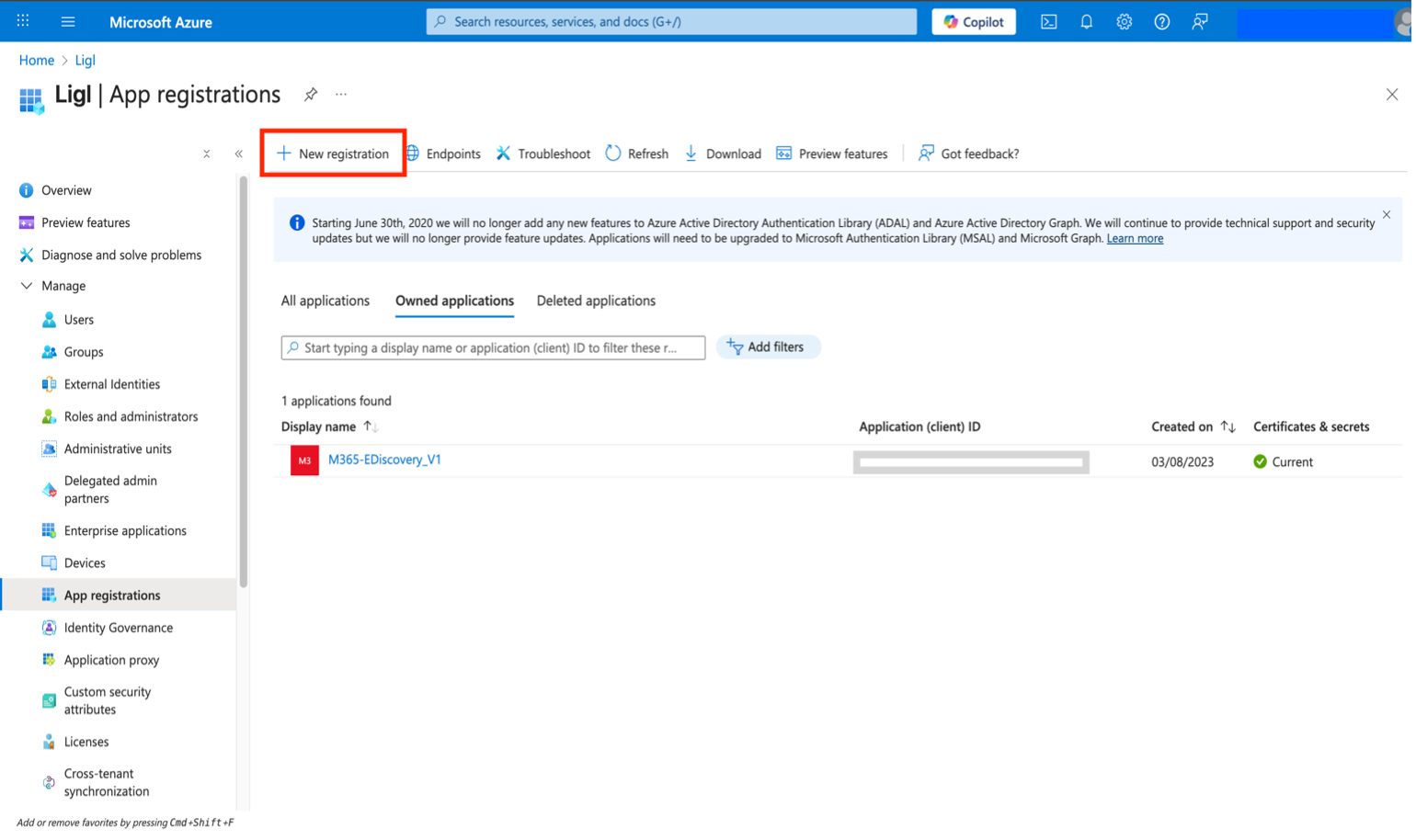
Figure: New Registration
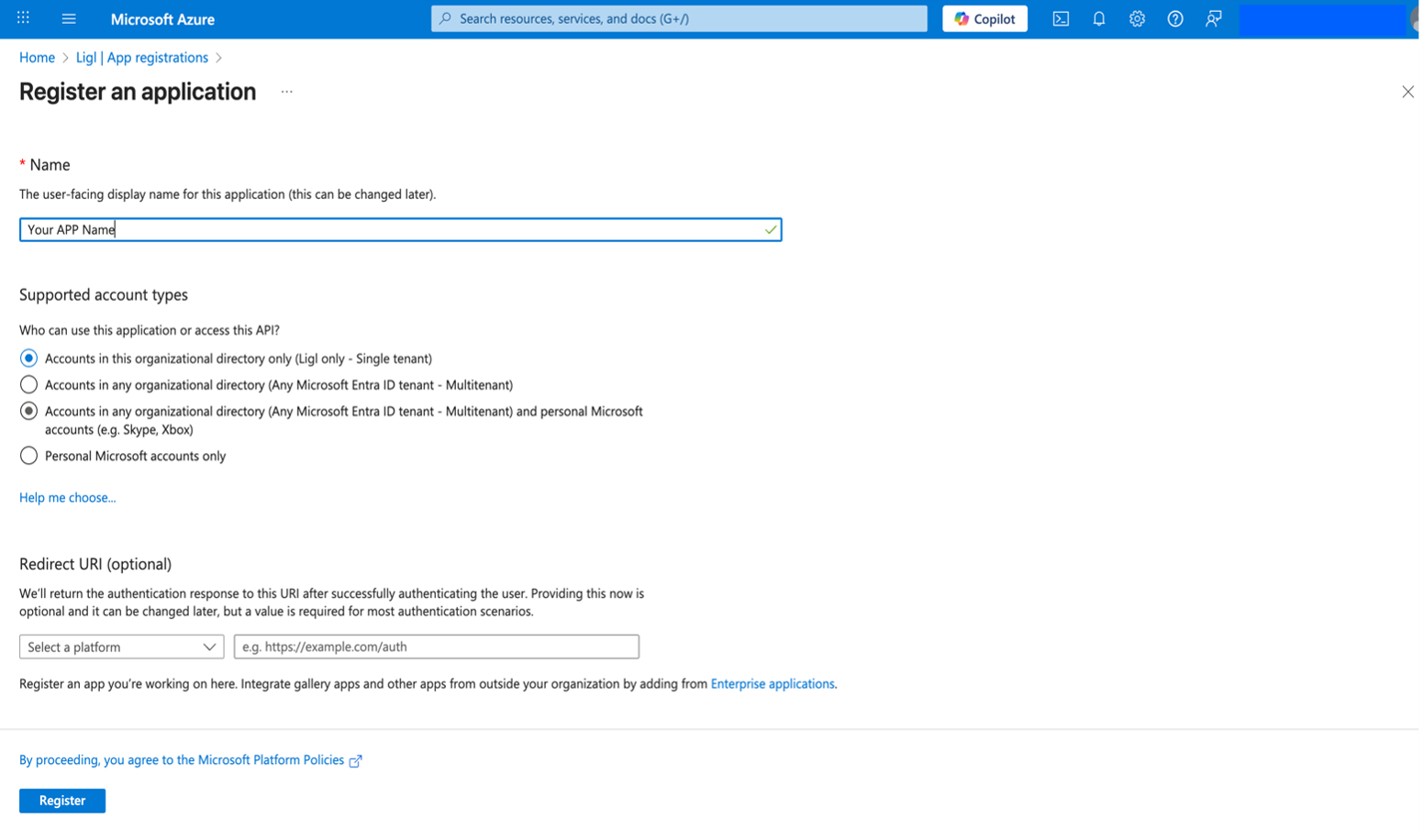
Figure: App Registration - Part 1
Enter a Display Name for the application. Users of the application might see the display name when they use the app, for example during sign-in. The display name can be changed at any time and multiple app registrations can share the same name. The app registration's automatically generated Application (client) ID, not its display name, uniquely identifies the app within the identity platform.
Specify Accounts in this organizational directory only can use the application. In some cases it is known as Sign-in audience.
Do not enter Redirect URI (optional). The following section describes how to configure a redirect URI.
Select Register to complete the initial app registration.

Figure: App Registration - Part 2
Once App is created, Note down ClientID and TenantID.
Add a Redirect URI
A redirect URI is the location where the Microsoft identity platform redirects a user's client and sends security tokens after authentication. In a production web application, for example, the redirect URI is often a public endpoint where the app is running.
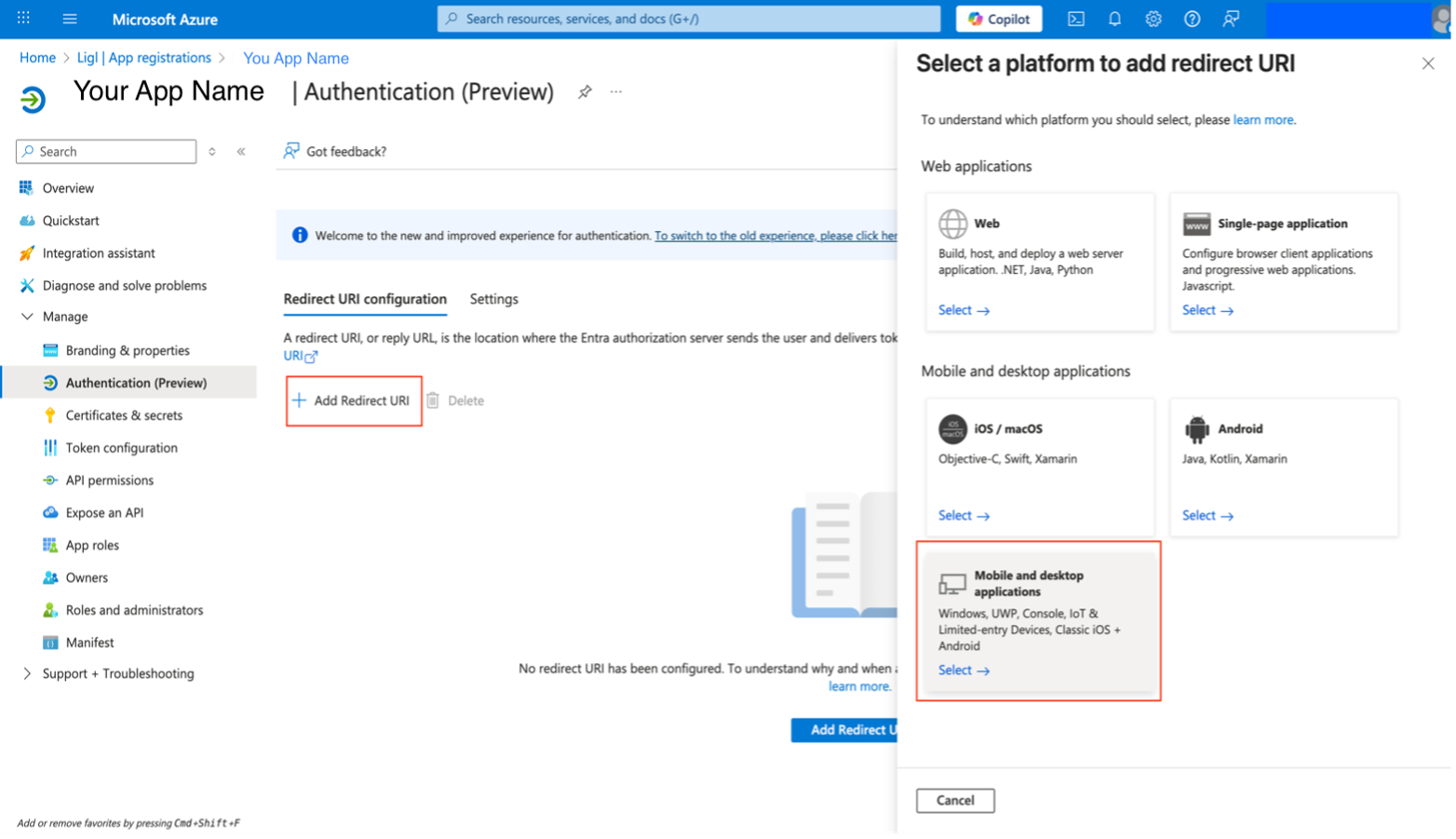
Figure: Redirect URI
Mobile and Desktop Applications
Select one of the suggested redirect URIs. For desktop applications using embedded browsers, https://login.microsoftonline.com/common/oauth2/nativeclient needs to be checked.
Select Configure to complete the platform configuration.
Add a Client Secret
The client secret is also known as an application password. It is a string value the app can use in place of a certificate to identify itself. The client secret is the easier of the two credential types to use.
To add a Client Secret, first select the application from App registrations in the Azure portal. Then follow the steps given below.
Select Certificates & secrets.
Select New client secret.
Add a Description and an Expiry for your client secret.
Select Add.
Record the secret's value for use in the client application code.
This secret value is never displayed again after leaving this page.
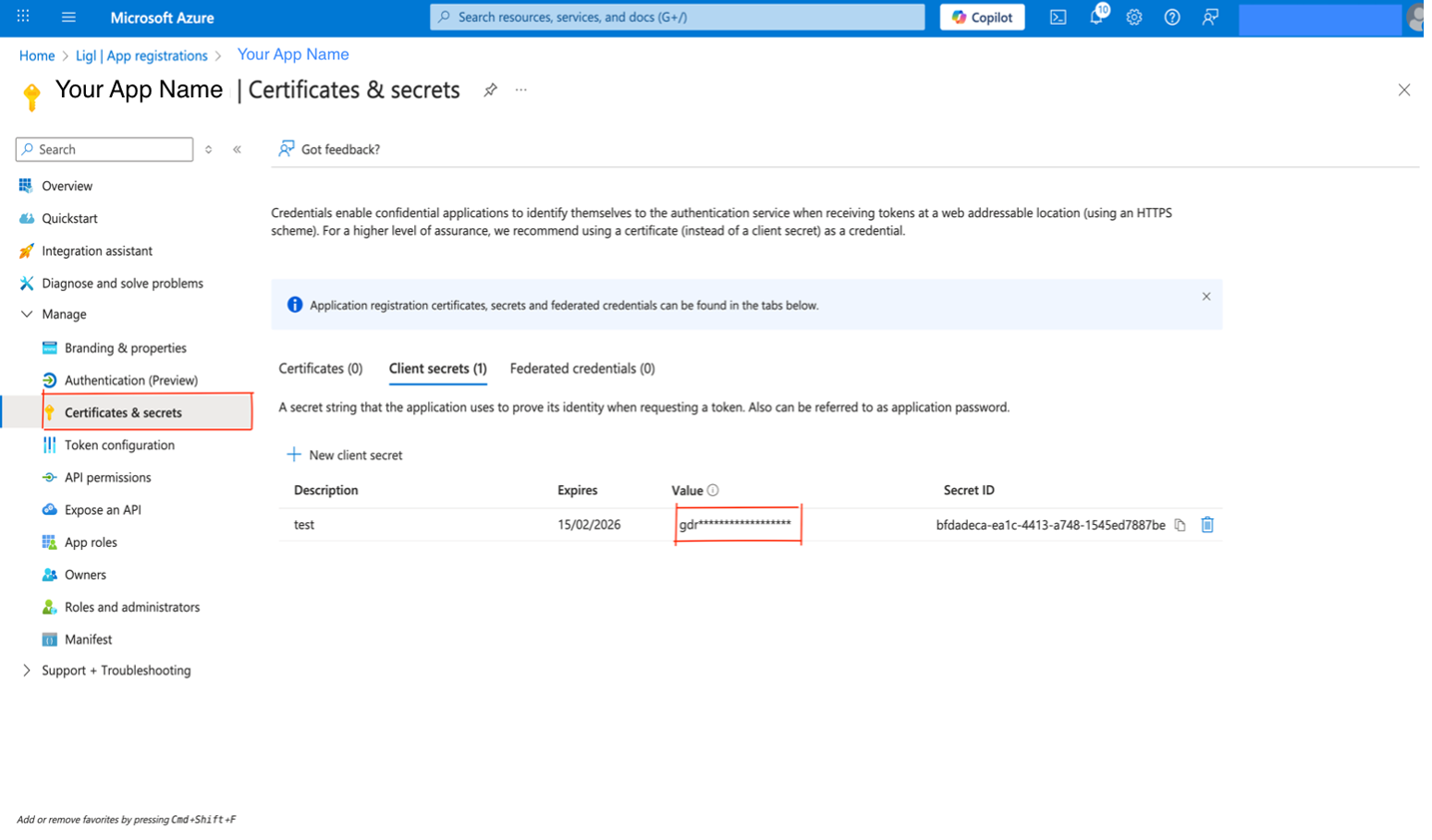
Figure: Certificates and Secrets
Add Permissions to Access Microsoft Graph
Configure delegated permission to Microsoft Graph to enable the client application to perform operations on behalf of the logged-in user such as reading their email or modifying their profile. By default, users of the client app are asked when they sign in, to consent to the delegated permissions configured for it.
To configure permissions:
Choose API permissions to view the options.
Select Add a permission > Microsoft Graph.
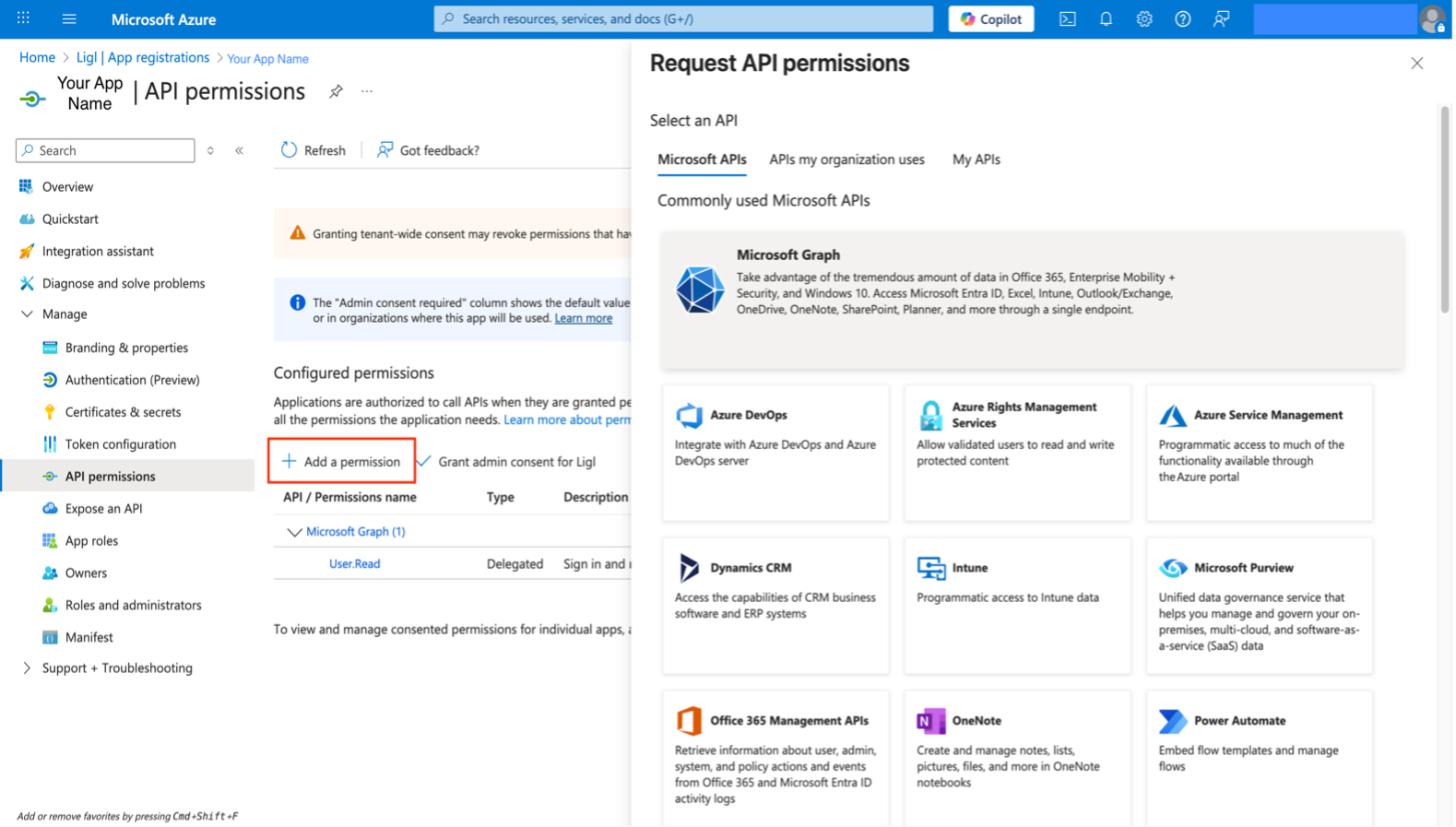
Figure: Add Permission - Microsoft Graph
Select Delegated permissions. Microsoft Graph exposes many permissions, with the most commonly used shown at the top of the list.
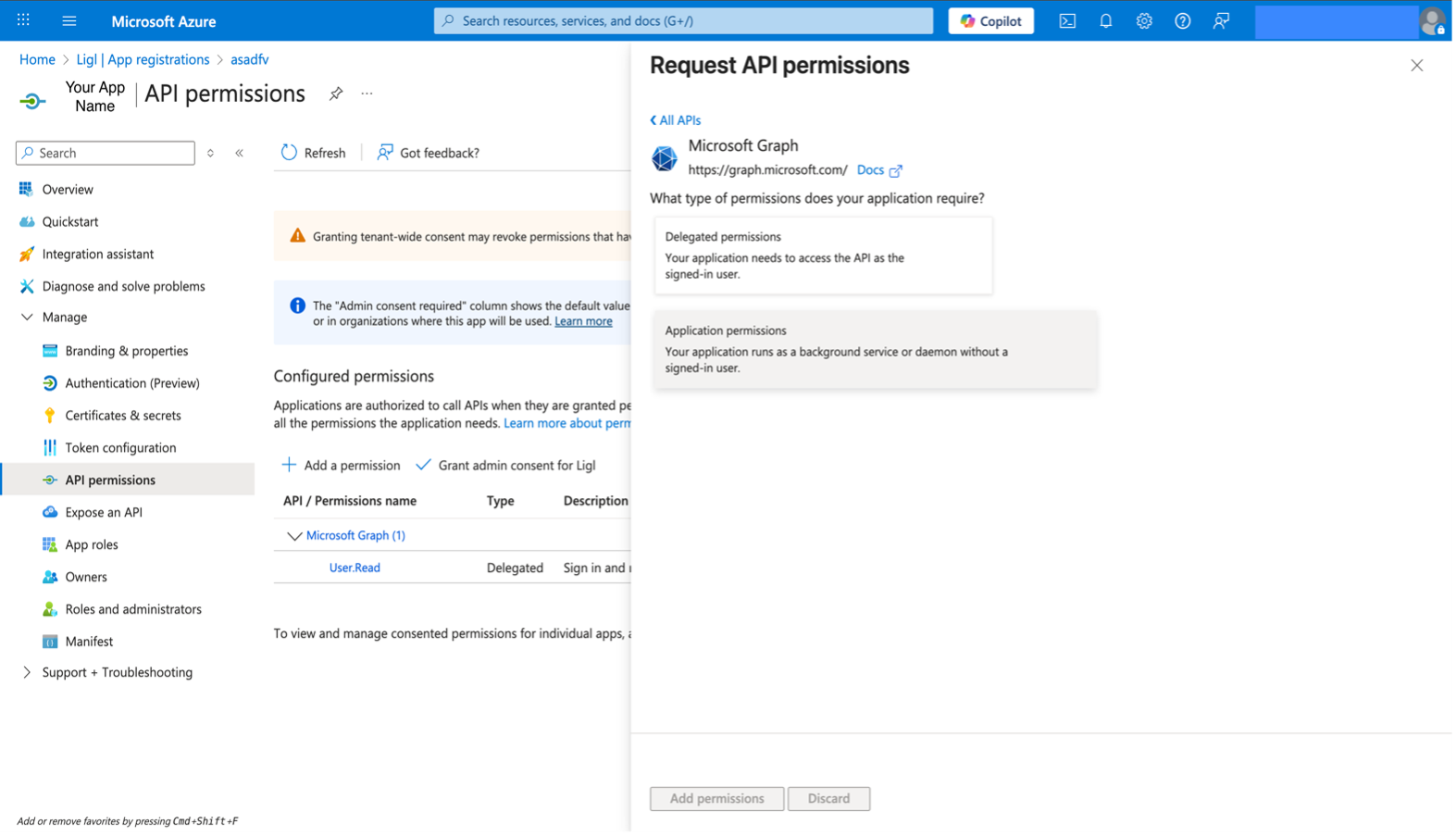
Figure: Delegated Permissions
Under Select permissions, select the following permissions and navigate to Application. Permissions adjacent to Delegated permissions to Select Application permissions listed in below table.
MicroSoft Graph (8)
API / Permissions name | Type | Description | Admin consent required |
User.Read.All | Application | Read all users’ full profiles | Yes |
User.Read.All | Delegated | Read all users' full profiles | Yes |
User.Read | Delegated | Read and write all eDiscovery objects | No |
Sites.Read.All | Application | Read Items in All Site Collections | Yes |
Group.Read.All | Application | Read All Groups | Yes |
EDiscovery.ReadWrite.All | Delegated | Read and Write All eDiscovery objects | Yes |
Directory.Read.All | Application | Read Directory Data | Yes |
EDiscovery.Read.All | Delegated | Read Case, Custodian Data | Yes |
MicrosoftPurviewEDiscovery (1)
API / Permissions name | Type | Description | Admin consent required |
eDiscovery.Download.Read | Delegated | To Download content | Yes |
Sharepoint (3)
API / Permissions name | Type | Description | Admin consent required |
Sites.Read.All | Application | Read items in All Site Collections | Yes |
User.Read.All | Delegated | Read all users’ full profiles | Yes |
User.Read.All | Application | Read all users’ full profiles | Yes |
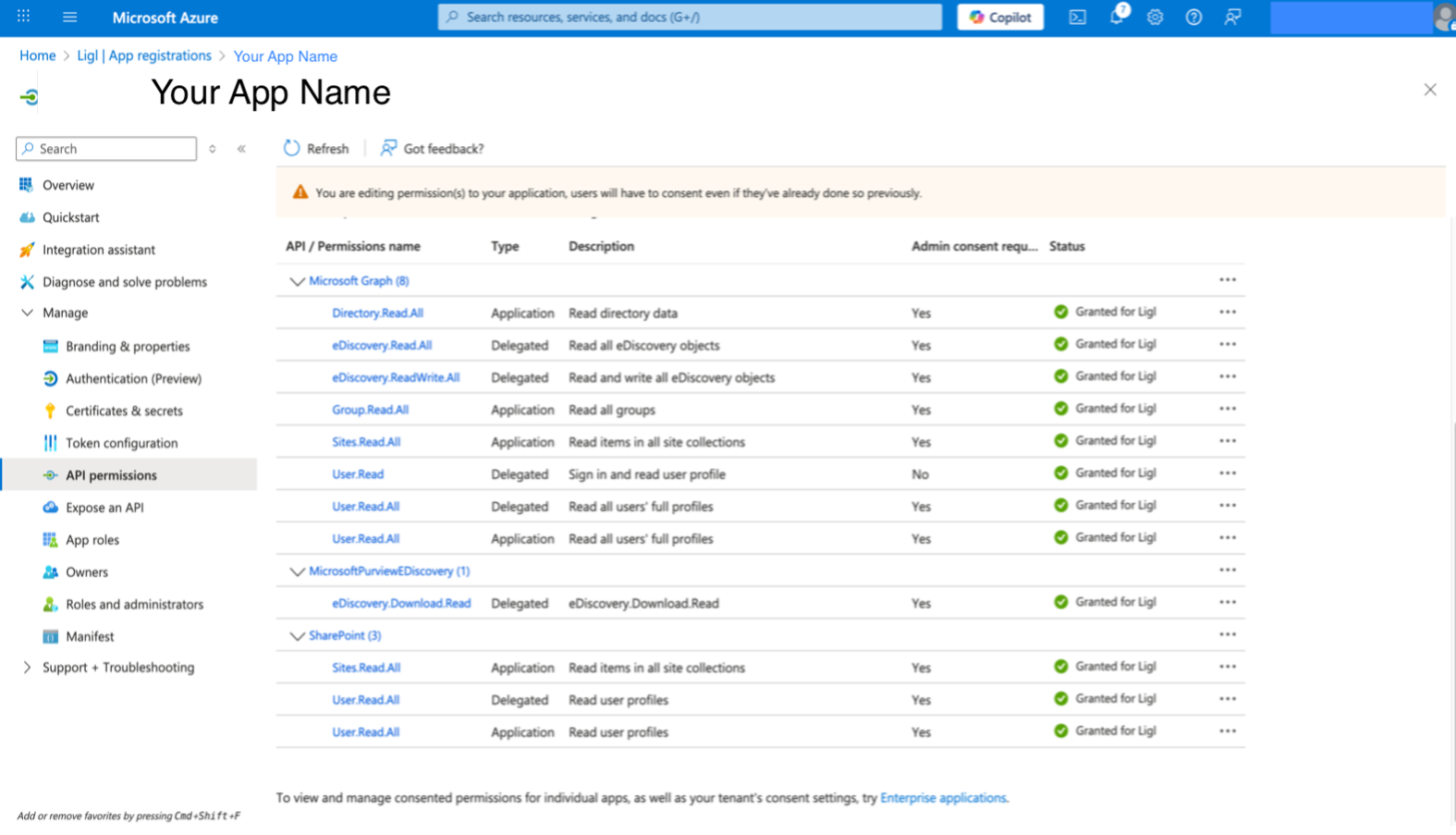
Figure: Configured Permissions
Add Permissions for collection using Microsoft Graph
We need to add one more permission named “eDiscovery.Download.Read” inside our enterprise app. In order to have that permission available we need to register a service principal on Azure tenant MicrosoftPurviewEDiscovery.
To allow downloading exports from Microsoft Purview, perform the following actions in Powershell:
To check and install Microsoft Graph Module, run the below command: if (-not (Get-Module -ListAvailable -Name Microsoft.Graph)) { Install-Module Microsoft.Graph - Scope CurrentUser -Force } else { Write-Host "Microsoft.Graph module already installed." }
Log in to Azure AD with PowerShell with the following command: Connect-Graph -Scopes "Application.ReadWrite.All" (Requires Global Admin Credentials)
Create a Service Principal for the MicrosoftPurviewEDiscovery application by running the following PowerShell command: New-MgServicePrincipal -AppId b26e684c-5068-4120-a679-64a5d2c909d9
To add this permission, we need to open our same app which we created earlier while doing Register Application in Azure.
After opening the app to configure permissions:
Choose API permissions to view the options.
Select Add a permission > API my Organization uses.
MicrosoftPurviewEDiscovery → Delegated permission → eDiscovery.Download.Read
Note:
If somehow “MicrosoftPurviewEDiscovery” is not searchable/visible while searching then search for “b26e684c-5068-4120-a679-64a5d2c909d9”.
.png)
Figure: Add Permission - Microsoft Graph
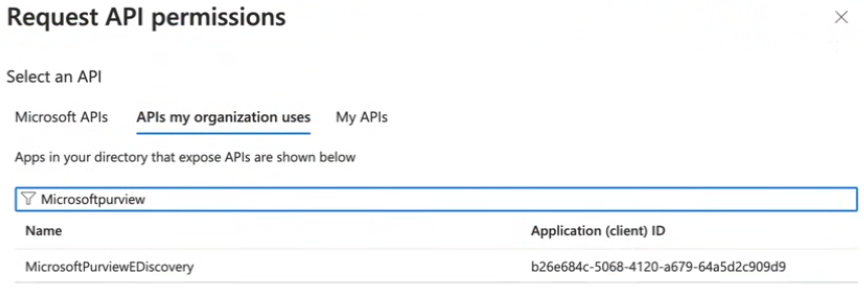
Figure: APIs my organization uses
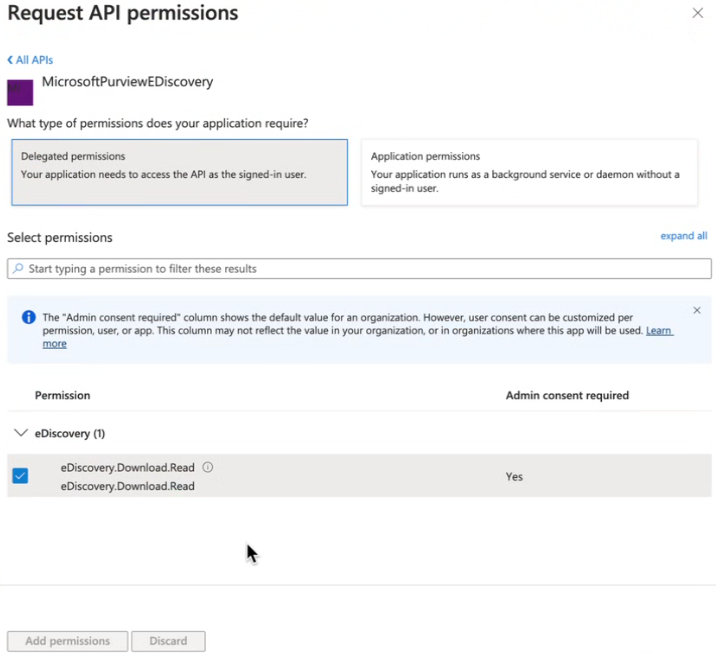
Figure: Delegated permissions- eDiscovery.Download.Read
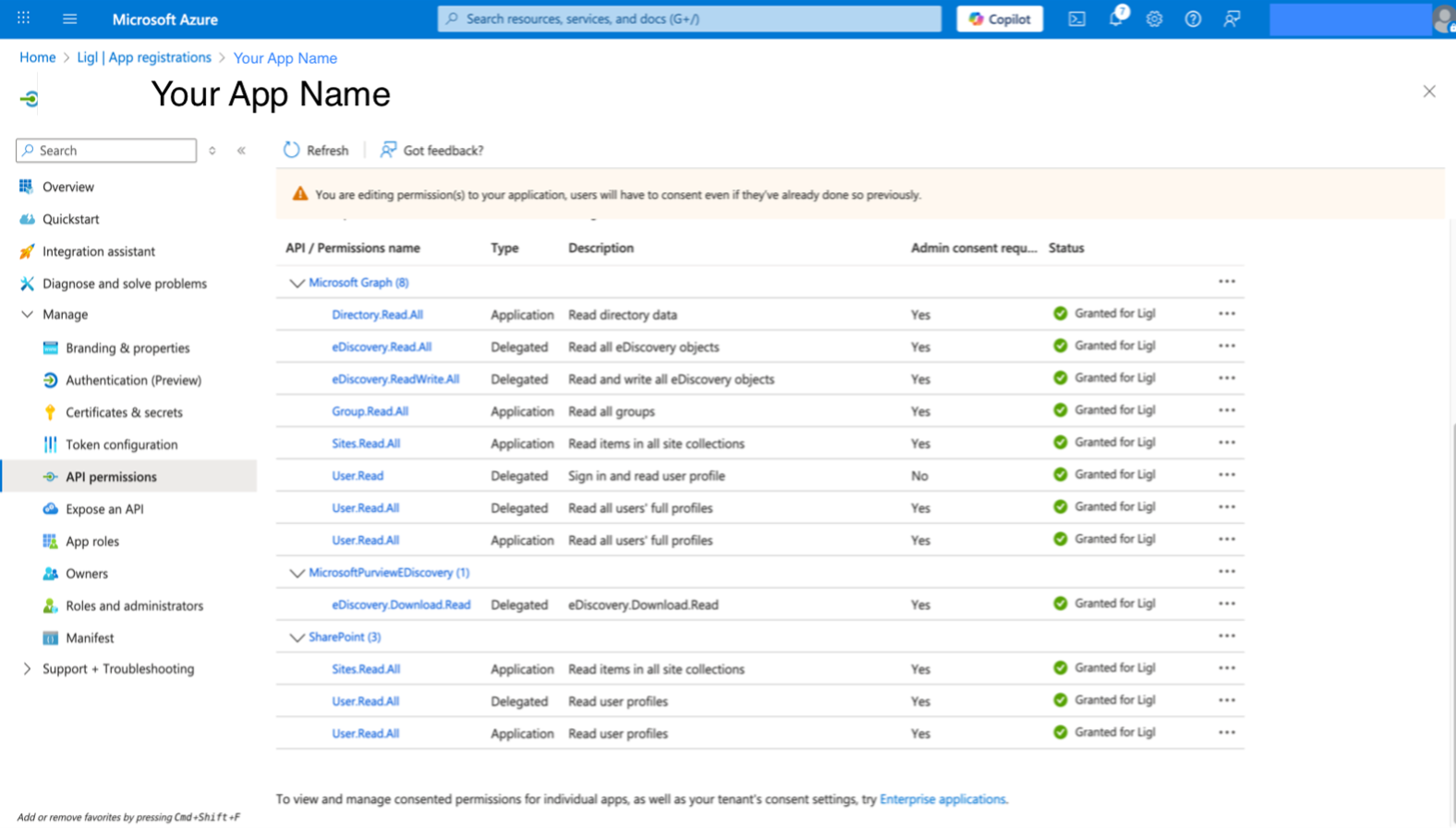
Final Api Permissions looks like the above Figure after giving “eDiscovery.Download.Read”